Fraud Management & Cybercrime , Governance & Risk Management , Remote Workforce
Data Breach Reports Fall 45% in UK
Are Organizations Failing to Spot Breaches, or to Report Them, as Required by GDPR?
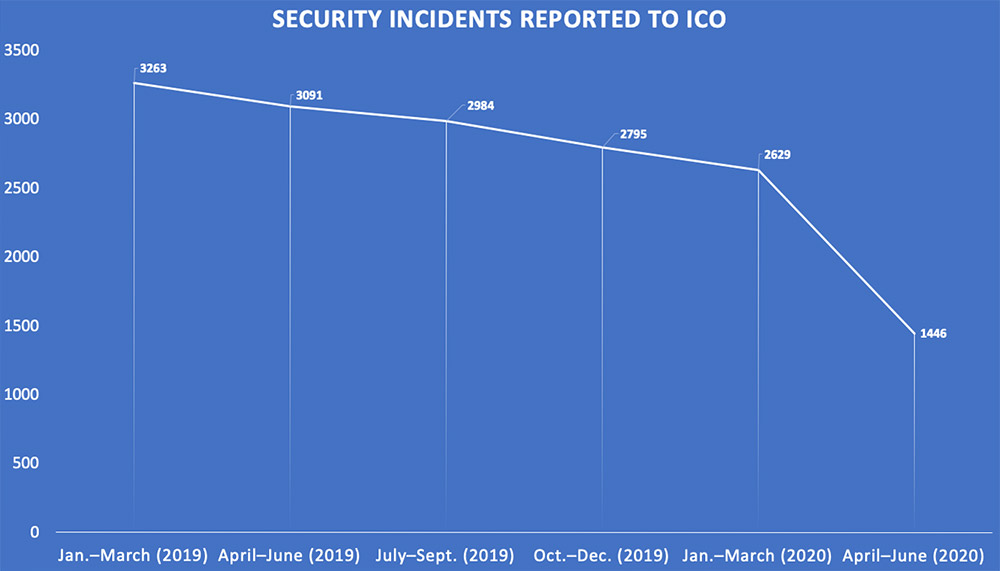
The number of cybersecurity incidents reported to the U.K.'s data privacy watchdog has continued to decline, recently plummeting by nearly 40%. But is the actual quantity of data breaches being experienced by organizations decreasing, or might they be failing to detect more breaches, or potentially even covering them up?
Those are some of the outstanding questions prompted by the latest release of data security incident trends published by the Information Commissioner's Office, which enforces Britain's data protection and privacy laws.
"These figures are based on the number of reports of personal data breaches received by the ICO during Q1 2020-21," it says, referring to the period from April through June. (The British government's fiscal year begins on April 1.) "These figures are based on the number of reports submitted by the data controller, not necessarily the number of incidents."
Applicable laws in the U.K. - including the EU's General Data Protection Regulation - require service providers, including data processors, to notify the ICO whenever a "personal data breach" occurs, referring to "a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data transmitted, stored or otherwise processed in connection with the provision of a public electronic communications service," according to the ICO.
"They must also notify customers if the breach is likely to adversely affect customers' privacy, and keep a breach log," it says.
Cybersecurity Incidents Decline by 37%
Comparing the April through June timeframe with the previous quarter, the total number of cybersecurity incidents reported to the ICO decreased by 37% - from 653 to 412 - while the number of non-cybersecurity incidents reported declined by 48%, from 1,976 to 1,034.
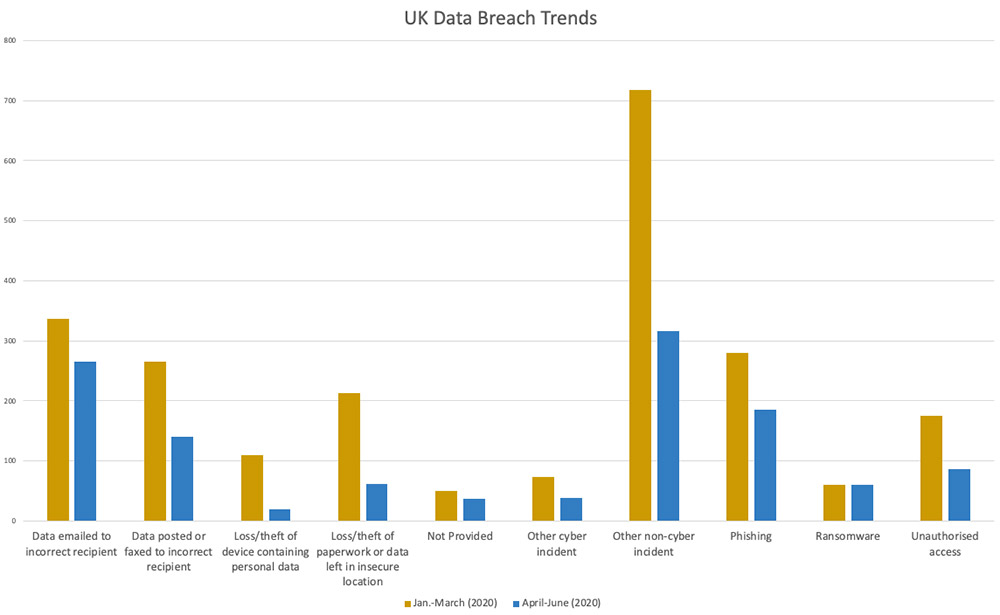
Further comparing the two quarters, here are some of the changes in causes of reported breaches:
- Phishing incidents dropped by 34%.
- Incidents caused by unauthorized access decreased by 50%.
- Hardware/software misconfiguration as a cause decreased by 80%.
- The reported number of ransomware incidents increased from 60 to 61.
- Incidents attributed to brute-force attacks increased by 38%, from 13 to 18.
What might account for the continuing, and recently substantial, decrease in reported incidents? The ICO didn't immediately respond to my request for comment.
Some other EU privacy regulators, however, have continued to receive ever-increasing numbers of security reports. Many security experts have also said the pace of attacks and incidents does not seem to have declined.
"We have not seen a decrease in the number of breaches," says Brian Honan, CEO of Dublin-based BH Consulting, whose comment is based on clients with which his firm works (see: Pandemic Impact: How Will Data Breaches Evolve?).
If anything, he says, the overall number of breaches might be increasing. But throughout the pandemic, physical breaches appear to be declining - understandable, since employees are not leaving laptops on buses or working with physical files. "However, we are seeing an increase in data breaches involving cloud-based systems, in particular, cloud-based email providers and file-sharing platforms," he says.
Breach Reporting in the COVID-19 Era
As many employees began working remotely in the spring, due to the COVID-19 pandemic, attackers also retooled to try to take advantage of this change. Security experts have been reporting a sharp rise in phishing attacks using coronavirus-themed lures as well as seemingly non-stop ransomware attacks (see: FBI: COVID-19-Themed Phishing Spreads Netwalker Ransomware).
Rick Goud, CEO of Amsterdam-based security communication firm Zivver, says the escalating online attack volume throughout the pandemic, coupled with a decrease in breach reports being received by the ICO, is cause for GDPR compliance suspicion.
"In a period with increased cyber threats, a big shift to working from home, with more digital communication and more employee behavior change - inevitably leading to more data leaks - this suggests that U.K. organizations don't see the necessity to comply with GDPR in terms of reporting data leaks, because the consequences of not complying are considered to be less costly than the alternative," he tells me.
Multiple Potential Explanations

But there could be multiple explanations for why U.K. breach reports have continued to decline since GDPR went into effect in May 2018 - and not just owing to a failure to report breaches.
"Another influence could be companies becoming more familiar with GDPR and better understanding the data breach thresholds that trigger the requirement to notify the ICO, and as a result they are reporting only those breaches that should be reported - as opposed to reporting all breaches, just to be on the 'safe side,'" Honan tells me.
The effect of the pandemic on workplaces' data processing has also been pronounced. "Many businesses have shut down either temporarily or permanently in the past six months; other companies may have laid off staff or furloughed them, or business activities processing personal data may have halted, which all could lead to fewer breaches," he says.
Detection Challenges
But the pandemic has surely also made life more difficult for IT teams. As a result, more breaches might be going undetected.
"In the rush to get businesses working remotely, the visibility the security and the data protection teams would have on activities - and potentially breaches - may be severely reduced," Honan says. "With IT teams working remotely, they may not have access to their appropriate security monitoring tools to detect a breach."
Potentially, security teams are also liaising less with legal teams. "There may also be a lack of understanding as to when a cybersecurity breach becomes a data breach - for example, an online email account hijacked by a criminal could expose personal data held in attachments to emails stored in the compromised email account," he says. "Some companies may consider this to be simply a breach of an email account - and not a potential data breach - due to the type of information that is stored within that mailbox."
With breach reports continuing to decline, security managers would do well to review their policies, practices and procedures and ensure they're not letting breaches go undetected or failing to report valid breaches to regulators.











